NIST Cybersecurity Framework - Comprehensive Compliance | CTG Tech Solutions
The NIST framework is a voluntary set of standards, guidelines and practices which helps organizations better manage their cybersecurity risks. NIST Cybersecurity Framework fosters risk management strategy among both internal stakeholders as well external parties involved in an organization’s network or digital assets while also helping larger companies integrate these efforts together into one integrated plan for greater effectiveness.
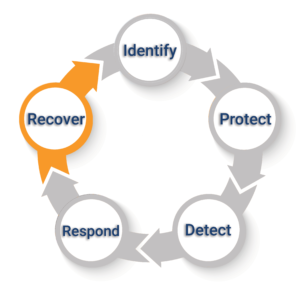
The Framework is organized by five key Functions. These Functions are: Identify, Protect, Detect, Respond, and Recover. These five terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity.
The Five Key Functions of NIST Cybersecurity Framework
-
Identify
The first step in the NIST Cybersecurity Framework
is to identify your critical processes and assets. It is important to ensure that you’re able to continue with business as usual and not lose anything vital if a situation were to occur.
Risk management is the process of identifying, assessing and documenting risks to assets. Risks can come from internal elements, such as an employee opening a phishing email and downloading a virus, or externally, such as threat actors who aim to harm your business.
Risk Assessments can be performed by your IT Professionals and will help you identify the best solutions for the risks your business faces.
Contact CTG Tech today to schedule your FREE Risk Assessment.
2. Protect
When employees need access to information, computers and/or applications, it is important that they are granted only the access they need. Keeping track of what each employee has access can prevent any improper usage, sharing confidential information, or destroying files.
Should your employees require access to be granted, or removed, it will be a simple fix from your MSP (Managed Service Provider).
3. Detect
Your company should have a way to detect unauthorized or suspicious activity on your network as well as physical environments.
CTG Tech takes time to understand how each client’s business operates, in order to know how the data is supposed to flow. Staying aware and understanding how critical business applications work allows us to be better equipped if something were to go wrong, or issues arise.
4. Respond
Ensuring each person understands what is expected of them allows a plan to be executed successfully. The more prepared your business is, the faster (and cheaper) recovery will be.
Maintaining an updated template for your response plan will ensure your company is prepared should any incident arise.
5. Recover
A crucial part of recovery is communicating all necessary information with the appropriate channels.
When an incident occurs and it’s not handled properly, your business’s reputation can suffer.




